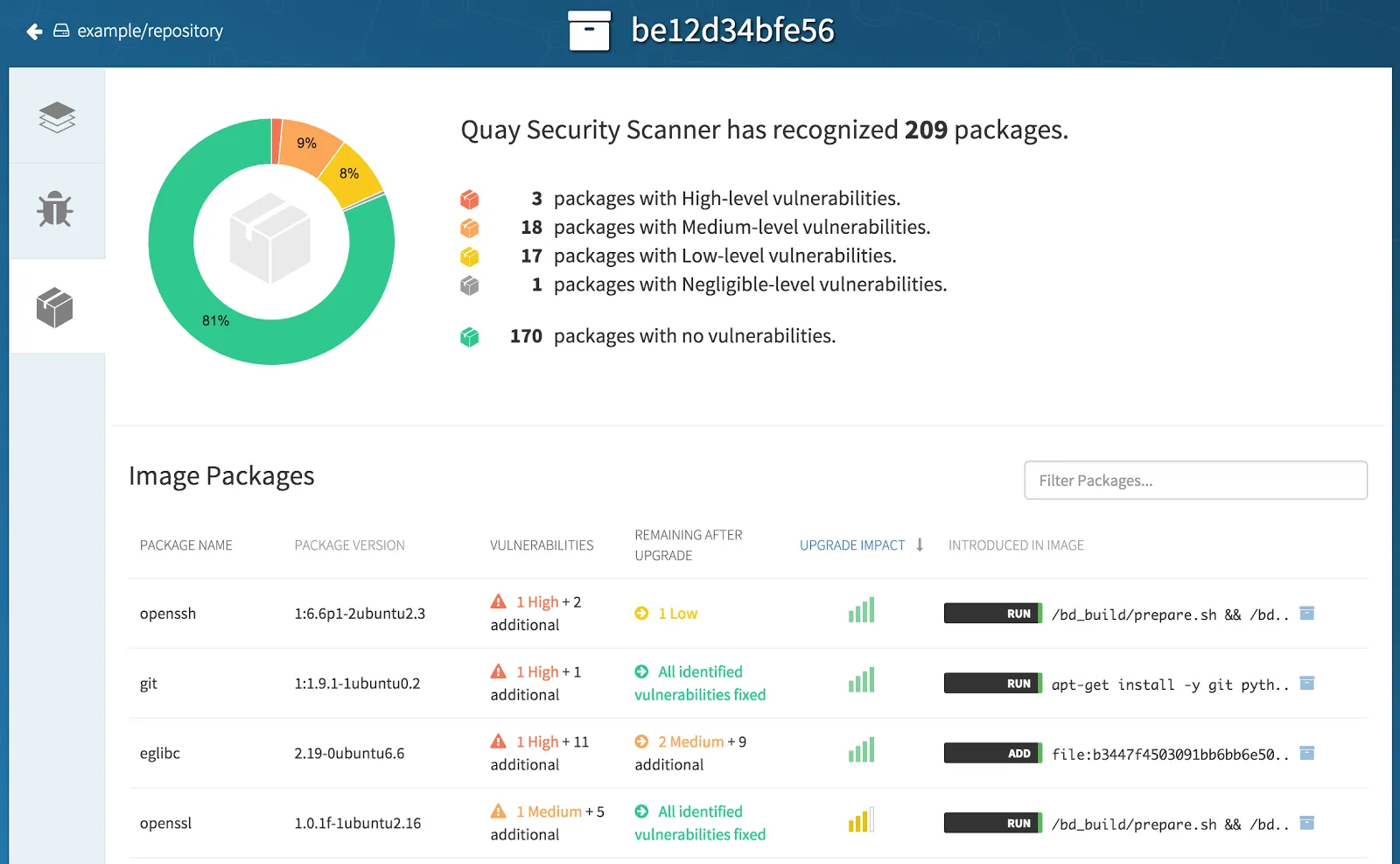
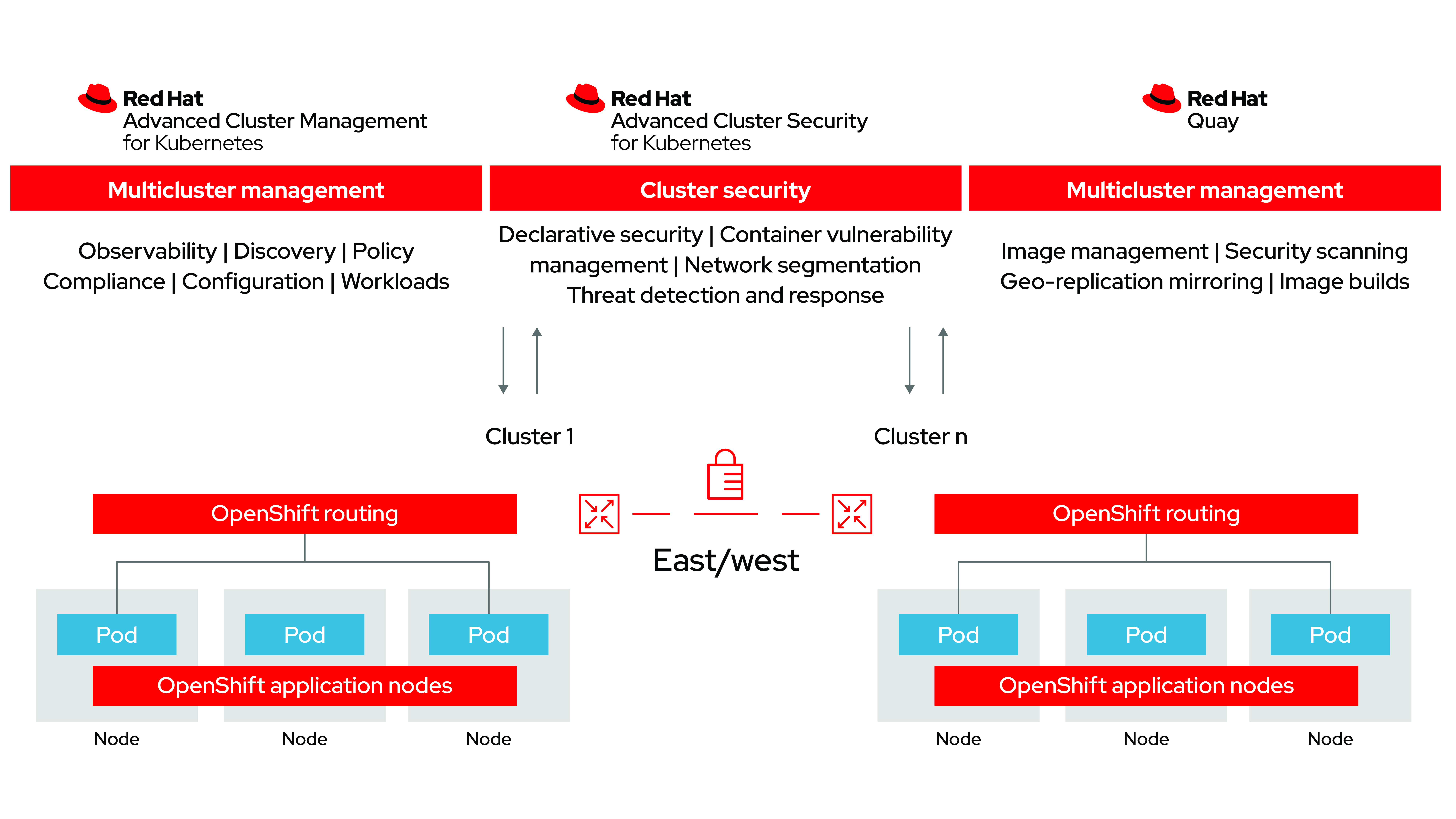
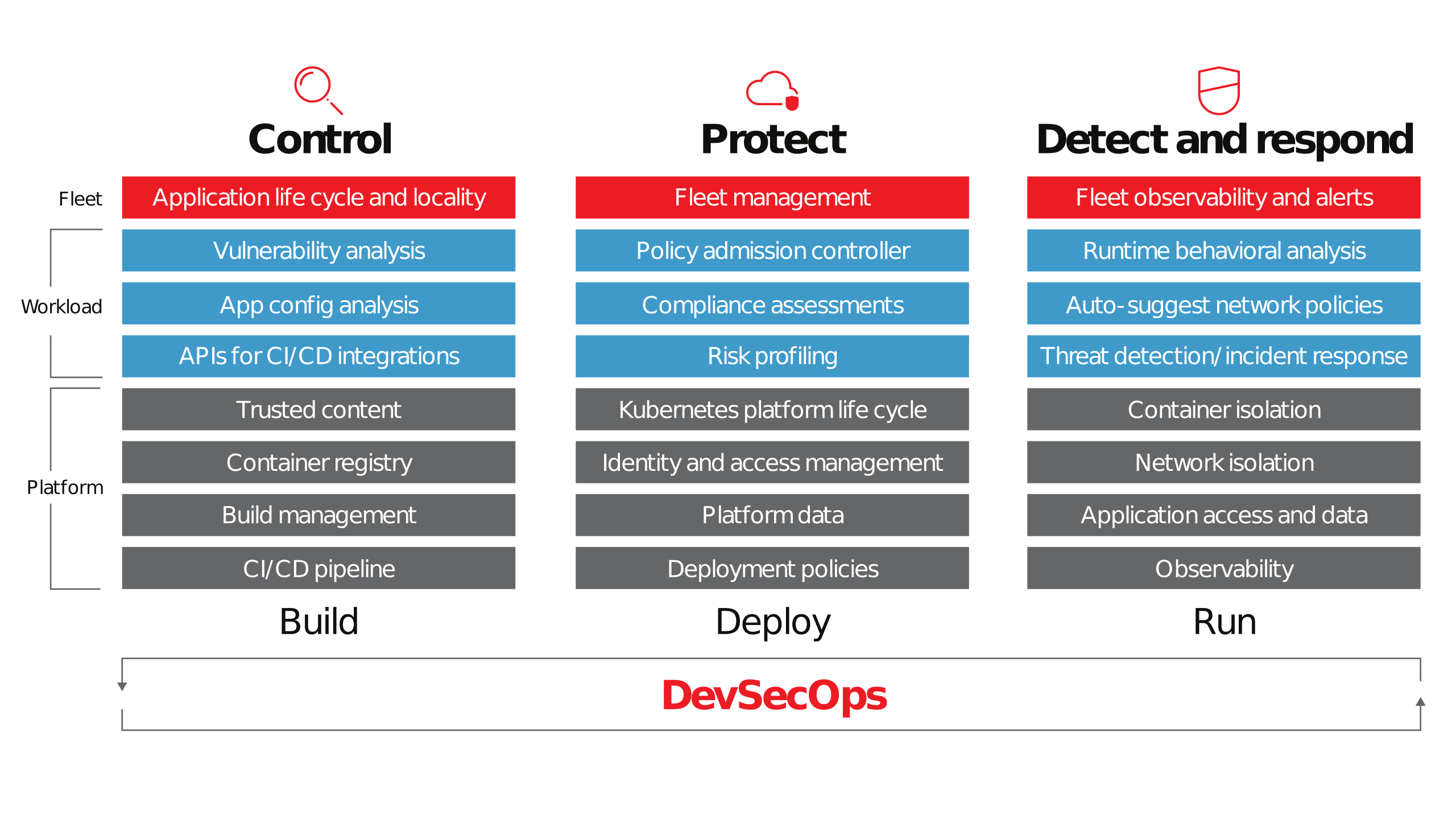
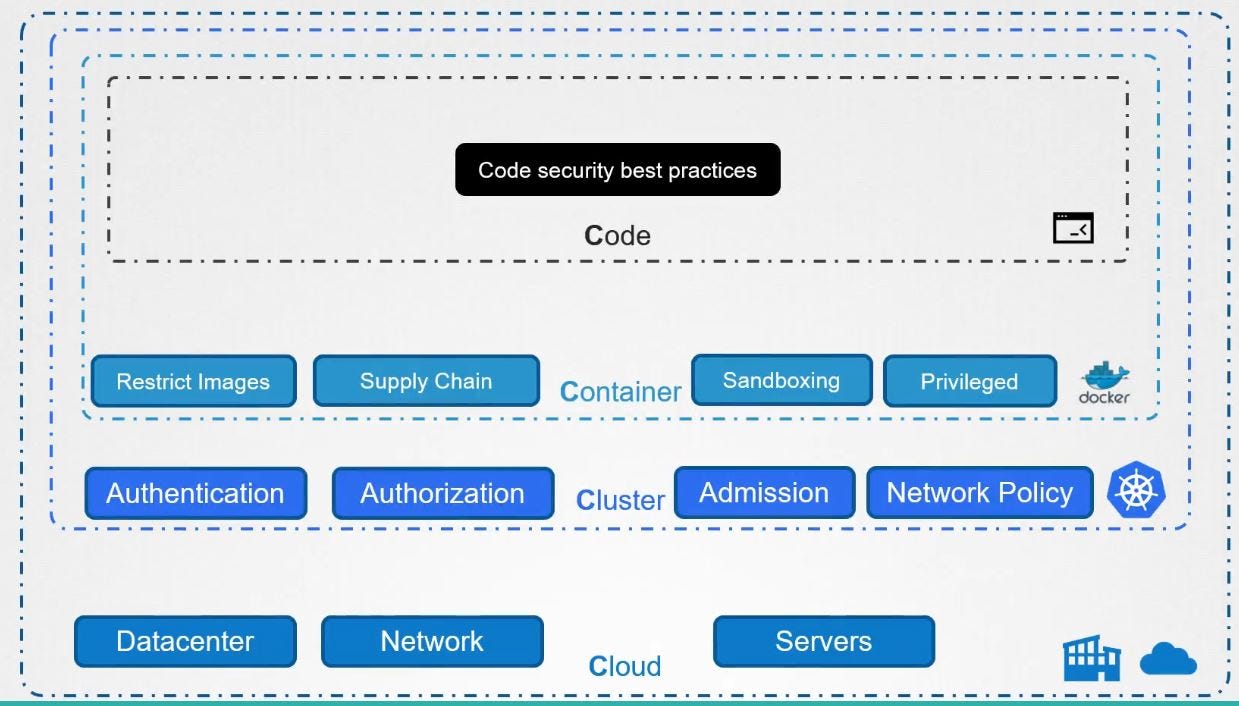
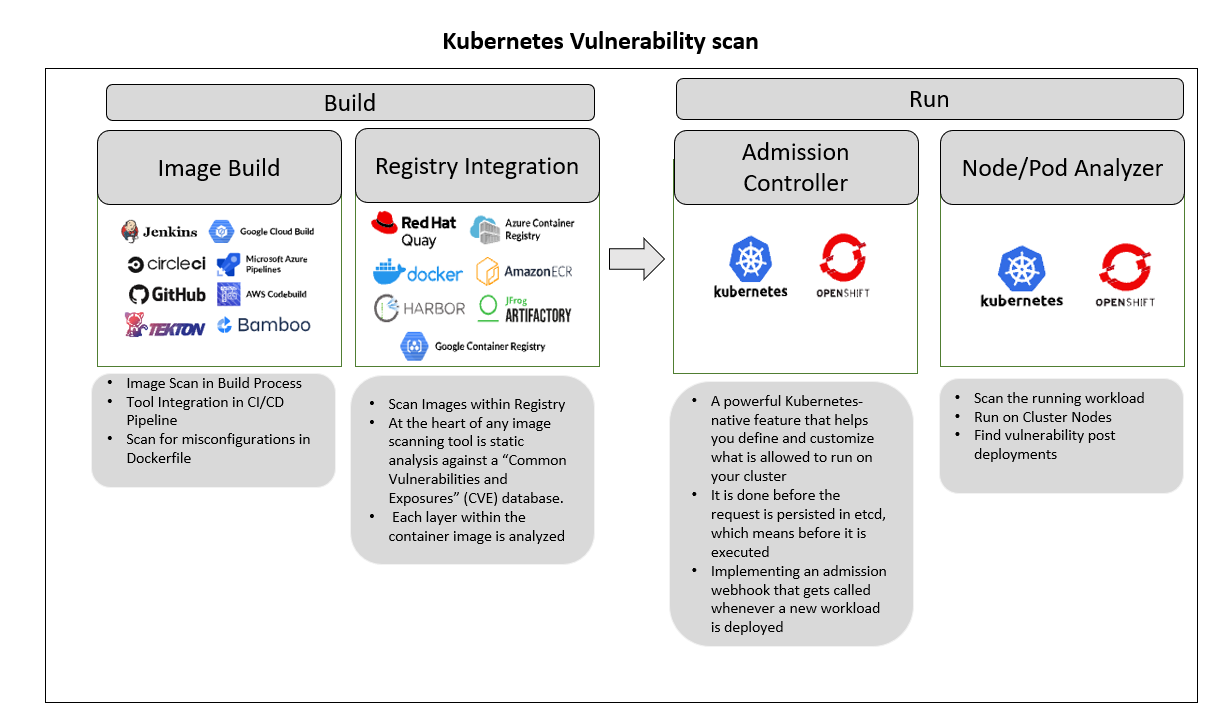
12 Scanners to Find Security Vulnerabilities and Misconfigurations in Kubernetes | by Walid El Sayed Aly | Towards Dev

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

12 Scanners to Find Security Vulnerabilities and Misconfigurations in Kubernetes | by Walid El Sayed Aly | Towards Dev